Hacking GSM is a lot of fun, USRP, GnuRadio, Airprobe, OpenBTS, etc. are really great tools.
I have successfully reproduced capture and analysis of my own GSM downlink traffic in one of the Czech 2G networks (on a BTS which happened not to perform frequency hopping during the test), using essentially the Karsten Nohl's HOWTO . Incoming SMS messages were also successfully received and displayed in plaintext by Wireshark.
HOW to intercept the cell phone - SIM card communication and read out the Kc key for GSM traffic decryption
When experimenting with GSM decryption, it is very useful to know the correct Kc key in advance to have a fixed point for debugging. This can be quite easily obtained by capturing and analyzing the phone-SIM communication.There are commercially available SIM adaptors, for example Turbo-kits by Bladox, which offer logging of the MS-SIM traffic, but a much cheaper solution with minimal hardware exists:
Take an expired pre-payed SIM card and using a micro-driller with an abrasive wheel (e.g. Proxxon) carefully grind out the plastic to expose back of the contacts of the SIM. Then solder a thin flat cable to the back side of the contacts and isolate it with insulation tape. When done carefully, the thickness will not be increased much and the SIM adaptor fits to the phone. There might be mechanical problems in some phones, but in my old Nokia 6310i it plugged in well. Pin-out of the SIM card can be found in the Wiki.
On the other side of the cable solder a little piece of universal PCB and connect the appropriate wires to corresponding pins of s SMD-mount SIM card socket. I have also added 100nF blocking capacitor between Vcc and GND and 680pF capacitor between Data and GND pins. The GND and Data signals go to a connector, to which a serial RS232 cable adapted to 3V3 level (like one would use to talk to a microcontroller) connects. Either you can adapt legacy RS232 port or USB-RS232 cable using MAX232CPE, or use a USB-RS232 chip like FT232BM without conversion to RS232 levels.
The setup looks like this:
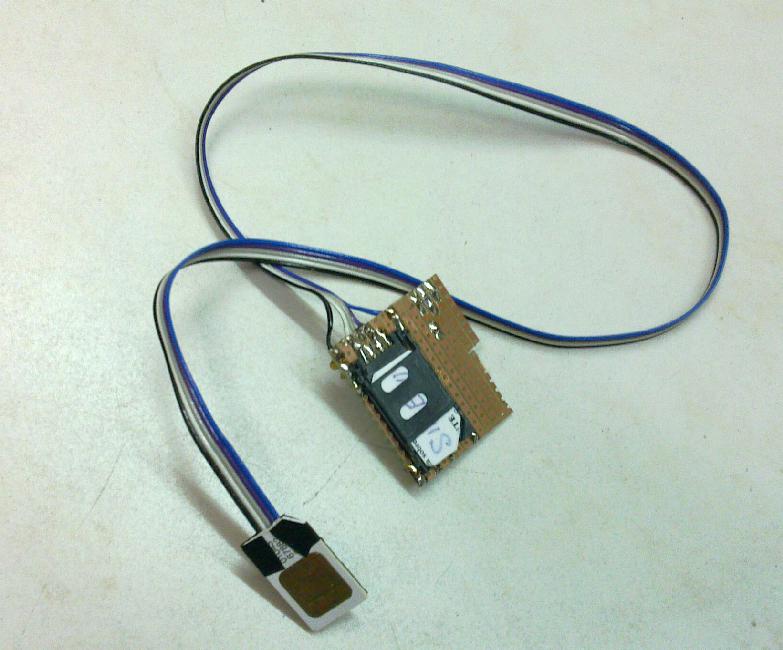

Now switch the phone on - it should recognize the SIM card - and using oscilloscope check the baud rate of the data being sent, since different phones might clock the SIM card at various frequencies. (For example, N6310i clocks it at 3.25MHz.)
The rest is software:
1. setserial /dev/ttyUSB0 spd_cust baud_base 24000000 divisor 2748
Adapt the divisor for your measured baud rate. Note that some USB-serial chips do not support the appropriate ioctl, use ttyS0 or FTDI USB adaptor if you have bad luck.
2. stty 38400 cstopb parodd -ixon -ixoff -crtscts cread clocal ignbrk -icrnl -opost -isig -icanon -iexten -echo -echoe -echok -echonl -noflsh -xcase -tostop -echoprt < /dev/ttyUSB0
Note: the setserial replaced 38400 by the custom baud rate
3. dump_sim < /dev/ttyUSB0
Here is the source of the trivial program which just flips and negates the bits: dump_sim.c
4. Look for a0 88 and a0 c0 GSM algorithm input and response to find the Kc
E.g. in the line a0 c0 00 00 0c c0 34 60 28 40 ad 6c 5f e4 bf 5c 20 00 90 00
Kc=ad6c5fe4bf5c2000
Notice the zero bits at the end, the result of an intentional weakening of the GSM encryption introduced in order to make the life of secret services easier :-).
Experiments with OpenBTS and Asterisk ... will be described later, not much time since it is just a hobby for me ...
For GSM experiments, I needed some simple antennas. I have constructed them myself, employing USRP as a simple antenna analyzer.
Something about receiving TETRA digital radio using RTL-SDR and USRP here.
Recommended reading on digital signal processing:
Steven W. Smith: The Scientist and Engineer's Guide to Digital Signal Processing, California technical publishing 1997, ISBN 0-9660176-3-3
Steven W. Smith: Digital Signal Processing: A Practical Guide for Engineers and Scientists, Elsevier 2003, ISBN 0-750674-44-X
Some useful internet references on Gnuradio and GSM
:Anatomy of GSM cellphone hardware
Catching and understanding GSM signals
Decrypting GSM
All your baseband belongs to us
USRP
Gnu Radio
Airprobe
OpenBTS
OpenLTE
ClockTamer
osmocomBB
DECT sniffing project
GSM ciphertext-only cryptanalysis
Hacking the newer type of SIM cards with COMP128v2 and COMP128v3
Announcement of SRLAB's remote (OTA) attack on vulnerable SIM cards
----------------
Back to my electronics page
My hobby page
My main page
TOP of my family pages