Exploring RFID technology with Proxmark3
RFID technology became rather ubiquitous in recent years, and its security has become topic of many studies. I decided to gain some hands-on experience in this topic and as a suitable tool I can recommend the Proxmark3 device, which is a universal LF/HF smartcard reader, writer, and emulator.
To install Proxmark, download the latest code from SVN repository:
svn checkout http://proxmark3.googlecode.com/svn/trunk/ proxmark3-read-only
cd proxmark3-read-only
vi common/Makefile.common and change CROSS prefix for your ARM crosscompiler (I have arm-none-eabi-, which I installed using crossdev on the Gentoo Linux)
make
make flash-os
make flash-fpga
Notice that this just uses the provided fpga/fpga.bit file. If you want to recompile the Verilog code, you have to install Xilinx Webpack (free of charge), see some hints here.
Notice also that I had troubles when I plugged Proxmark to a USB3 port or to USB2 via a HUB - plug it to a USB2 port directly in the computer!
Start the client program:
client/proxmark3
Check whether antennas are OK
proxmark3> hw tune
#db# Measuring antenna characteristics, please wait.
# LF antenna: 23,23 V @ 125.00 kHz
# LF antenna: 9,80 V @ 134.00 kHz
# LF optimal: 28,47 V @ 122,45 kHz
# HF antenna: 12,63 V @ 13.56 MHz
Now you can issue further commands - see the Proxmark documentation ...
Here is my Proxmark setup with quick and dirty antennas - but they work well.
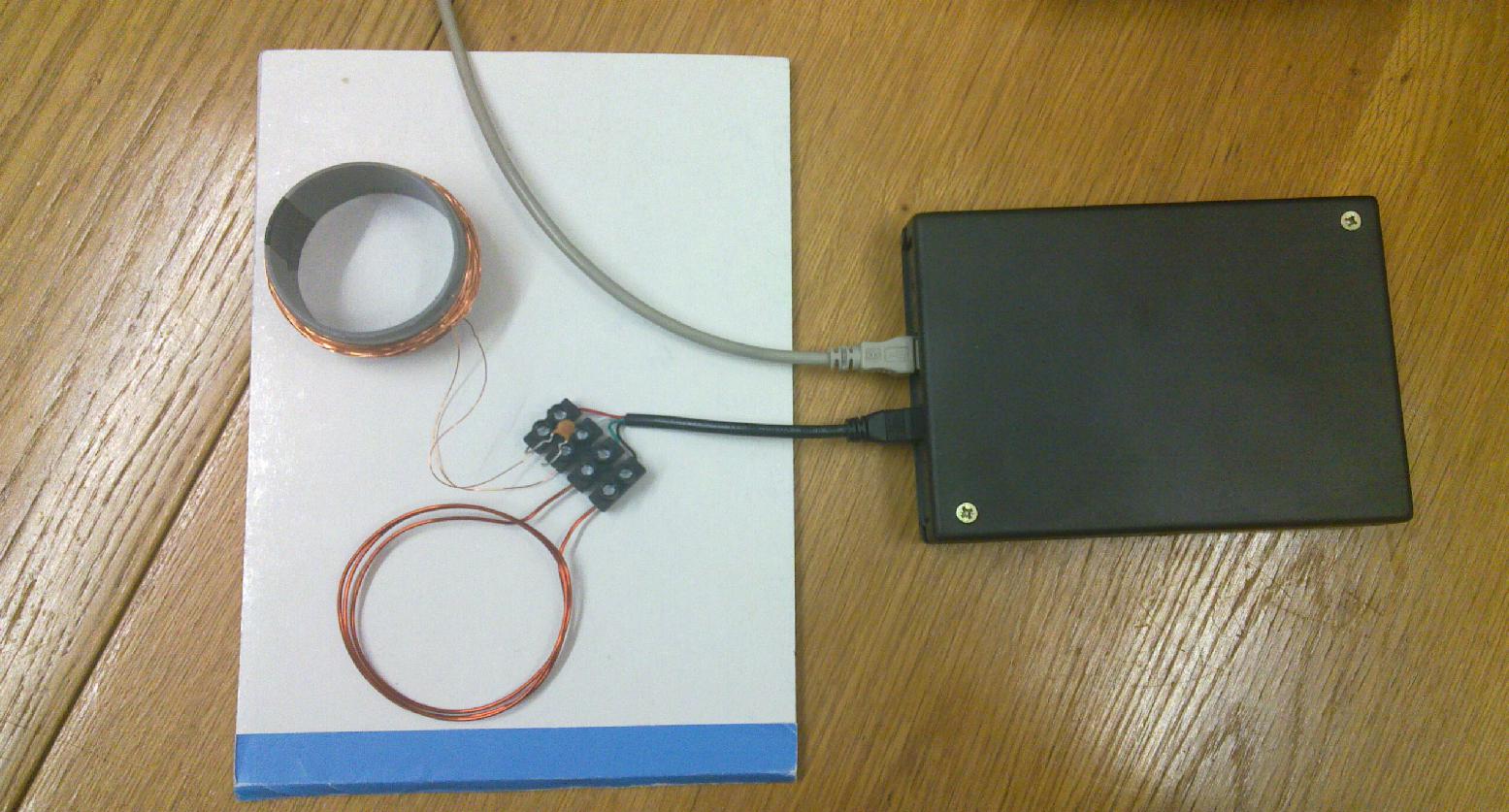
I did not have much time for RFID experiments recently; I have just successfully reproduced the Mifare classic cracking with some old RFID card for keyless building entry. I have also checked which files are stored in a Czech biometric passport and that a hash of the data signed by the State Printing Works of Securities of the Czech Republic (active authentication) is present. I have tested also a few examples of the Prague "Opencard" public transport card (btw. a project rather famous as a corruption case in our country that become rather expensive for Prague city), but all of them were already Mifare Desfire, which can probably be cracked by side-channel cryptanalysis, but that is nontrivial and requires different tools.
NOTE: In the meantime Mifare DESFIRE has been hacked, see links below.
Moreover, not all RFID formats are presently supported by Proxmark, one example being the proprietary LEGIC protocol (www.legic.com), which is being used for example in RFID locks sold by Kaba.
Here are some further links to useful programs and papers (not all of them support Proxmark, but a PCSC compatible reader is needed anyway if you want to test Proxmark as emulator) and information from the RFID field:
PCSC tools
OpenMRTD
LIBRFID
RFIdiot
Epassport
NFC tools
Timo Kasper's PhD thesis on Security analysis of pervasive wireless devices which covers the recent side channel cryptanalysis of Mifare Desfire RFID cards, which are widely employed (e.g. Prague's Opencard for public transport) Notice that the side channel cryptanalysis of RFID cards is much more technically demanding than that of, say, Keeloq chips.
ISO 14443 emulator based on ATxmega MCU
Maybe more information will be added during time...
My Electronics page
My hobby page
My main page with e-mail contact
TOP of my family pages